Enhancing Security Controls for Typical Windows Accounts

Enhancing Security Controls for Typical Windows Accounts
By default, standard users on Windows can run programs with elevated privileges if they enter an administrator password when prompted by User Access Control (UAC).
However, this is not the only behavior that the UAC has for standard user accounts, and you can change it depending on how secure these accounts are and the environment the computer is in. We’re going to show you how.
Disclaimer: This post includes affiliate links
If you click on a link and make a purchase, I may receive a commission at no extra cost to you.
The UAC Behaviors Available for Standard User Accounts
Unlike when changing UAC behaviors for administrator accounts , the behaviors for standard user accounts are a little more limited. According to the Microsoft Learn website, here are the behaviors you can choose and what they mean:
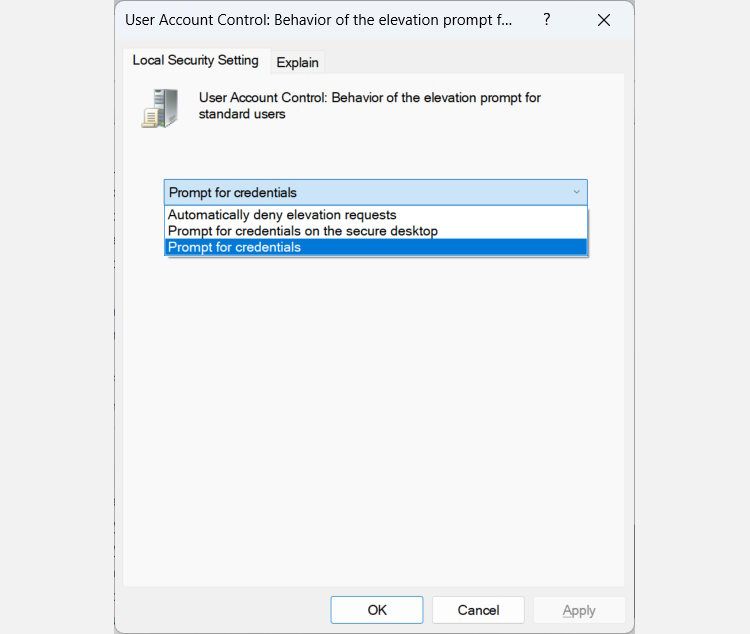
- Automatically deny elevation requests: This option returns an Access denied error message to standard users when they try to perform an operation that requires elevation of privilege. Most organizations that run desktops as standard users configure this policy to reduce help desk calls.
- Prompt for credentials on the secure desktop: When an operation requires elevation of privilege, the user is prompted on the secure desktop to enter a different username and password. If the user enters valid credentials, the operation continues with the applicable privilege.
- Prompt for credentials: An operation that requires elevation of privilege prompts the user to type an administrative username and password. If the user enters valid credentials, the operation continues with the applicable privilege.
The default UAC behavior for standard user accounts is Prompt for credentials, but Microsoft recommends you change it to Automatically deny elevation requests. That way, only users with administrator accounts can decide how the UAC behaves and make choices that will keep the computer safe.
How to Change the UAC Behavior for Standard Users in the Local Group Policy Editor
The easiest way to change the way UAC behaves for standard users is to tweak the User Account Control: Behavior of the elevation prompt for standard users policy. To do that, open the Local Group Policy Editor and follow the steps below.
The Local Group Policy Editor isn’t available by default on Windows Home. As such, check out how to access the Group Policy Editor on Windows Home before continuing.
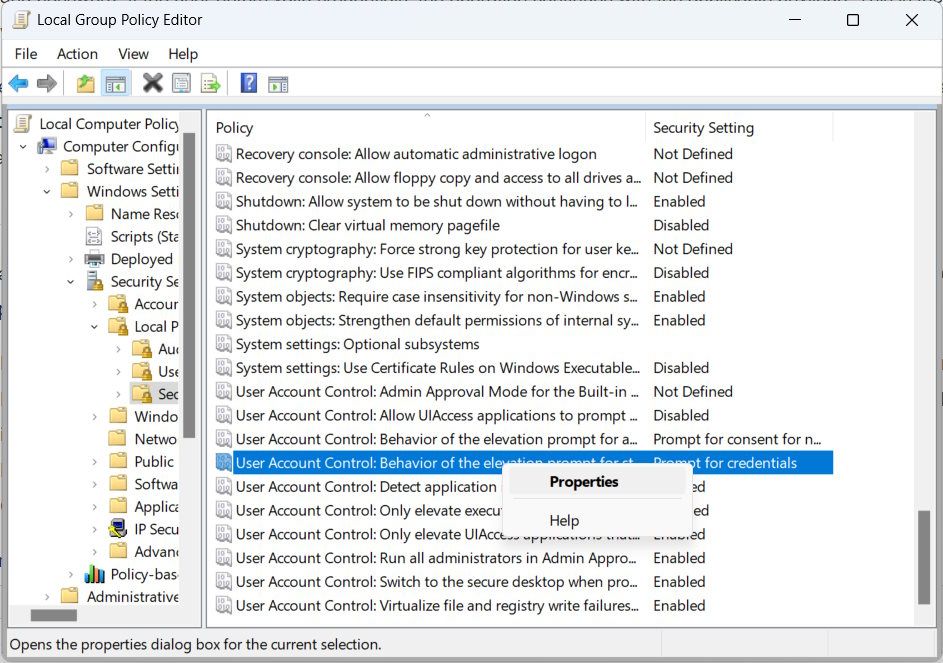
- Head to Computer Configuration > Windows Settings > Security Settings > Local Policies > Security Options.
- Right-click the User Account Control: Behavior of the elevation prompt for standard users policy and select Properties in the menu.

- Expand the dropdown and choose a different UAC behavior.

- Click OK.
Keep in mind that only administrators can change the behavior of the UAC. If a standard user tried to change it using the Local Group Policy Editor, for example, they’d probably get an Access denied error message.
How to Change the UAC Behavior for Standard Users in the Registry Editor
If you’re looking for another way to change UAC behavior for standard users, or the Local Group Policy is not working on your computer, you can make changes in the Windows registry instead.
Before you do that, however, we recommend you create a system restore point to protect your computer in case you make a mistake. Once you do that, open the Registry Editor and follow the steps below:
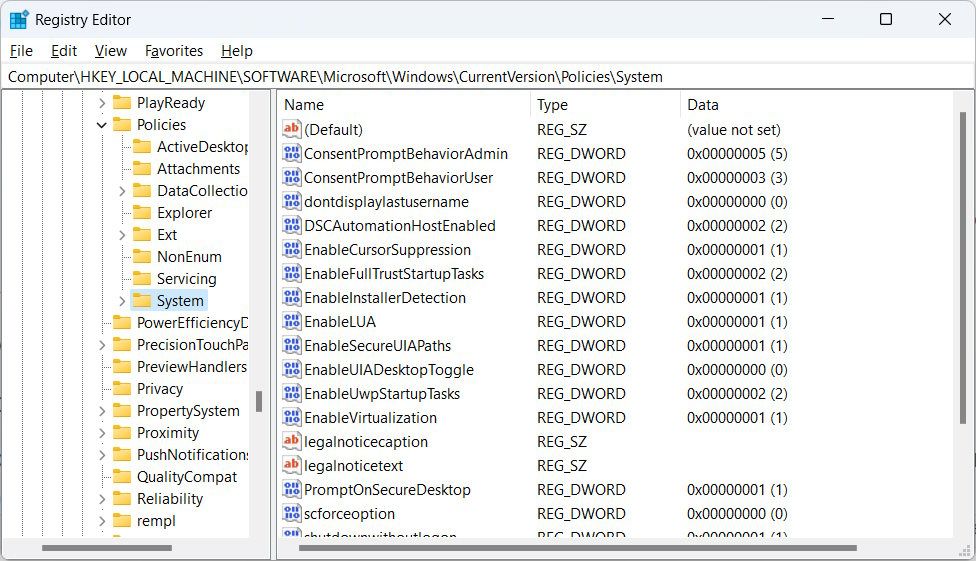
- Copy HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System and paste it into the address bar at the top of the Registry Editor.

- Press Enter on your keyboard to go to the System key.
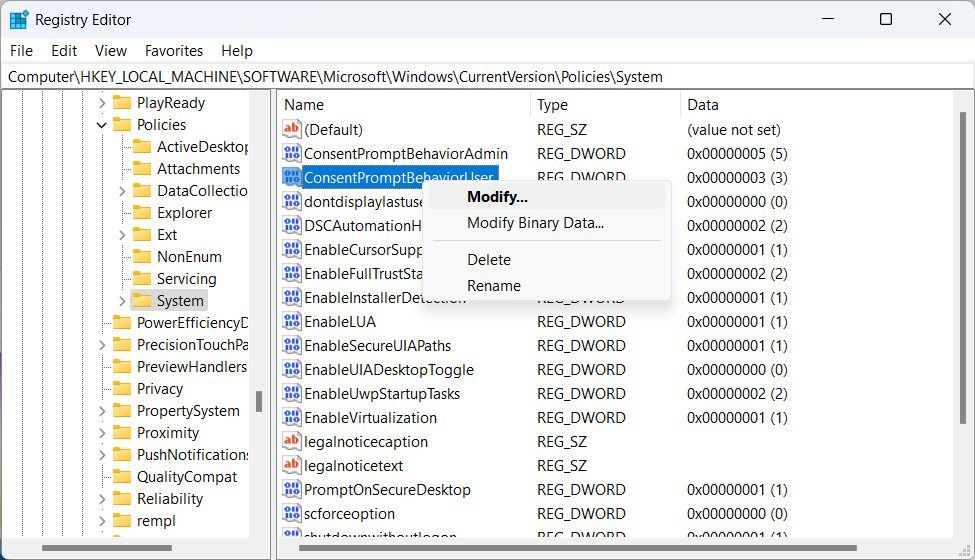
- Right-click the ConsentPromptBehaviorUser value in the right panel and select Modify.

- In the Value data text box, enter 0 for Automatically deny elevation requests, 1 for Prompt for credentials on the secure desktop, or 3 for Prompt for credentials.
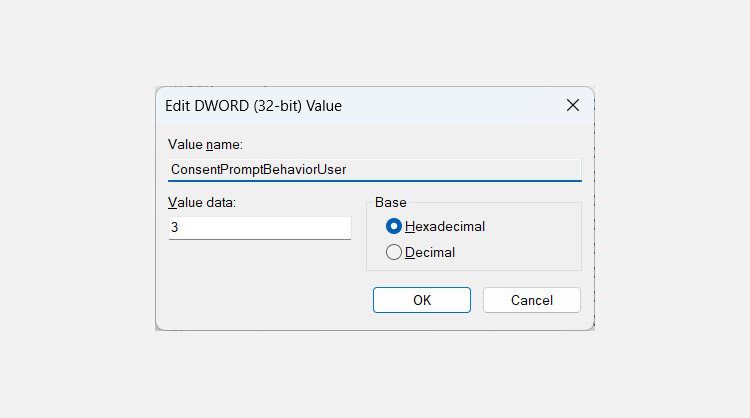
5. Click OK.
Now restart your computer to allow the changes to take effect.
Control UAC’s Behavior for Standard Users on Windows
UAC is an integral part of protecting your Windows computer from malicious programs that want to run with elevated privileges. While you can’t make it elevate programs without prompting, you can make it stricter by setting it to Automatically deny elevation requests. And, as you can see, it is quite easy to do, whether you’re using the Local Group Policy Editor or the Registry Editor.
However, this is not the only behavior that the UAC has for standard user accounts, and you can change it depending on how secure these accounts are and the environment the computer is in. We’re going to show you how.
Also read:
- [New] Discover Engaging, Free Slide Shows with These Amazing Template Selections
- [Updated] 2024 Approved Essential Recording Tools - Top 5 Webcam Capturers
- 2024 Approved Maximizing iPhone-to-Mac File Transfer for Large Videos
- 7 Essential Steps for Dealing with Windows' HTTP Error 0X80860010
- A Step-by-Step Method for Clean Booting on Windows 11 Systems
- Addressing Excessive TiWorker.exe CPU Usage Issue
- Addressing the Hang Issue: DXGI_ERROR_DEVICE_HUNK on Windows
- Analyzing the Strengths of Win11 in Compare with MacOS
- Augmenting Task Manager Functionality in Windows 11 with CLI
- Chrome Opening Woes Resolved: Fast Fixed for Windows 11 Users.
- Comprehensive GameSir X2s Type-C Evaluation: Ideal Hand Size Irrelevant
- Dual Virus Scanners? Think Twice, Windows
- Harnessing ChatGPT's Capabilities for Poetic Expression
- How To Erase Private Data From iPhone 14 | Dr.fone
- Mastering the Airwaves DJI Drones and Social Media Live for 2024
- Scambiare File Video MP4 Con MKV Senza Costi: Guida Completa Di Movavi
- Streamline Your Listening Experience: Swift Techniques to Download Music From VK Platforms
- Tame Frozen Windows-Handbraked Beast!
- マップされたネットワークドライブバックアップ:Windowsサーバー方法
- Title: Enhancing Security Controls for Typical Windows Accounts
- Author: Richard
- Created at : 2024-11-14 17:23:29
- Updated at : 2024-11-17 18:06:27
- Link: https://win11-tips.techidaily.com/enhancing-security-controls-for-typical-windows-accounts/
- License: This work is licensed under CC BY-NC-SA 4.0.