
Seven Crucial Windows Functions to Monitor Vigilantly

Seven Crucial Windows Functions to Monitor Vigilantly
Processes are an unavoidable part of Windows, and it is not unusual to see dozens or hundreds of them in Task Manager. Each process is a program or part of a program that is running. Unfortunately, malware creators know this and are known to hide malicious software behind the names of legitimate processes.
Here are some of the most commonly hijacked or duplicated processes, along with where they should be located and how to spot a malicious version.
Disclaimer: This post includes affiliate links
If you click on a link and make a purchase, I may receive a commission at no extra cost to you.
1. Svchost.exe
The Service Host, or svchost.exe, is a shared-service process. It allows various other Windows services to share processes. This helps to reduce resource usage, making the system more efficient. You will almost certainly see more than one instance of Svchost.exe in Task Manager, but this is normal. If one or more of these files are compromised by malware, you may notice a distinct reduction in performance.
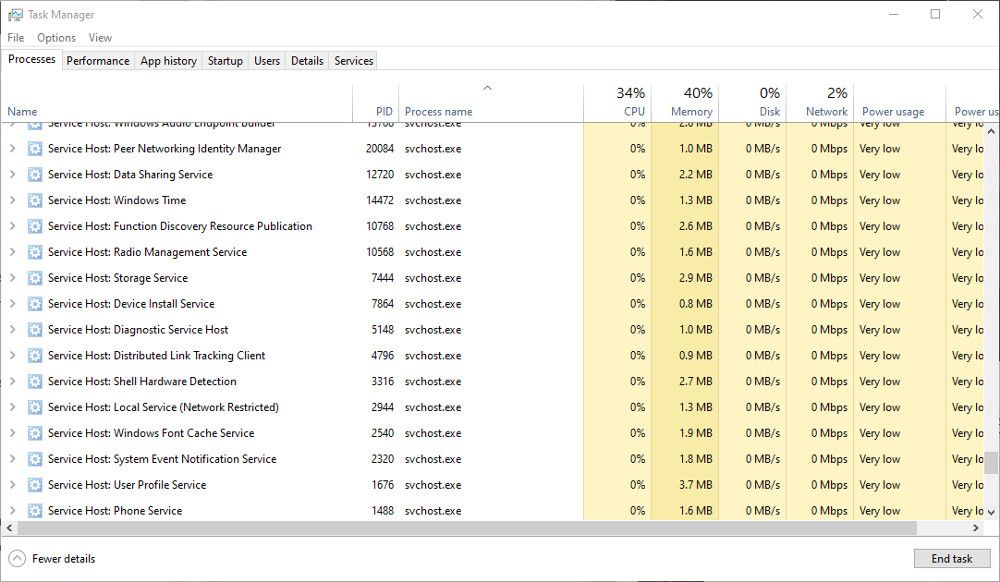
The legitimate Svchost files should be found inC:\Windows\System32 . If you suspect it has been hijacked, checkC:\Windows\Temp . If you see svchost.exe here, it could be a malicious file. Scan the file with your antivirus software, and quarantine it if necessary.
2. Explorer.exe
Explorer.exe is responsible for the graphical shell. Without it, you would have no Taskbar, Start Menu, File Manager, or even the Desktop. Therefore, it is an essential part of Windows and cannot be disabled.
Several viruses can use the Explorer.exe filename to hide behind, including trojan.w32.ZAPCHAST. The legitimate file will be inC:\Windows . If you find it inSystem32 , you should definitely check it with your antivirus software.
3. Winlogon.exe
The Winlogon.exe process is an essential part of the Windows OS. It handles things like loading the user profile during login and locking the computer when the screensaver runs. Unfortunately, because it handles security elements, Windows Logon and the winlogon.exe process are common targets for threats.
Several Trojan viruses, including Vundo, can be hidden within or disguised as winlogon.exe. The usual location of the Winlogon.exe file isC:\Windows\System32 . If you find it inC:\Windows\WinSecurity , it could be malicious. One good indication that the process has been hijacked is unusually high memory use.
Viruses and malware don’t just hide behind Windows processes. Here are someother ways malware can go undetected and hide on your computer .
4. Csrss.exe
The Client/Server Run-Time Subsystem, or Csrss.exe, is an essential Windows process. Although it is not as widely used in modern Windows versions, it is still required by the system and cannot be disabled.
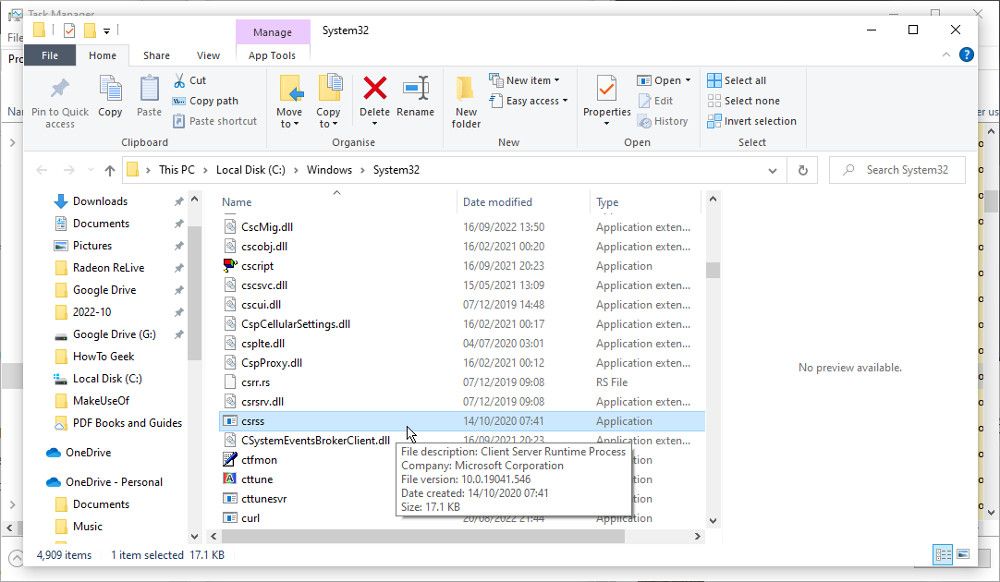
The Nimda.E virus has been known to mimic the Csrss.exe process, although that is not the only potential threat. The legitimate file should be located in theSystem32 orSysWOW64 folders. Right-click on the Csrss.exe process in Task Manager and chooseOpen File Location . If it is located anywhere else, it is likely to be a malicious file.
5. Lsass.exe
lsass.exe is an essential process responsible for the security policy on Windows. It verifies the login name and password, among other security procedures. It is unlikely that the process will be hijacked. If it isn’t running correctly, you will usually be automatically logged out of your computer. But viruses are known to use the filename to hide.
Look for the Lsass.exe file inC:\Windows\System32 . This is the only place you should find it. If you see it in another location, such asC:\Windows\system orC:\Program Files , act with suspicion and scan the file with your antivirus.
6. Services.exe
The Services.exe process is responsible for starting and stopping various essential Windows services. Like the other Windows processes in this list, viruses and malware target it because it allows them to hide in plain sight.
If the file is hijacked, you may notice problems during the startup and shutdown of your PC. Look for the real Services.exe file in theSystem32 folder. If it is located anywhere else, such as inC:\Windows\ConnectionStatus , the file could be a virus.
The processes mentioned here are essential to the smooth running of Windows. But not all are, and many non-essentialprocesses can even be closed to help with performance .
7. Spoolsv.exe
The Windows Print Spooler Service, or Spoolsv.exe, is an important part of the printing interface. It runs in the background, waiting to manage things like the print queue when required. The process is not dependent on having a printer connected, so you shouldn’t be surprised to see it in Task Manager.
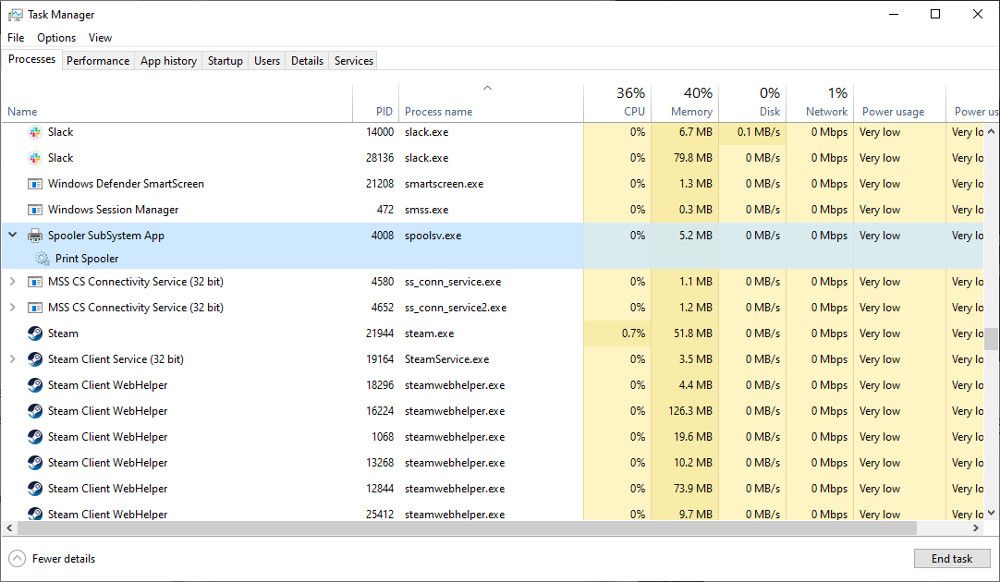
Perhaps because Spoolsv.exe is easily overlooked, a virus can take the name to make itself seem legitimate. The true spools file can be found inC:\Windows\System32 . The fake file will often appear inC:\Windows , or in a user profile folder.
How Do You Check if a Process Is Legitimate?
The Task Manager is your friend when looking for suspicious activity. Infected processes will often behave erratically, consuming more CPU power and memory than is usual. But that isn’t always the case, so here are some other ways to check a process is legitimate.
Most of the essential processes listed here should only appear in the System32 folder. You can easily check the location of a suspicious file in the Task Manager. Right-click on the process and selectOpen File Location . Check the path of the folder that opens to ensure the file is in the correct place.
Another way to tell if a file is legitimate is to check the size. Most of the .exe files of these essential processes will be under 200kb. Right-click on the process name in Task Manager, selectProperties and look at the size. If it seems unusually large, take a closer look to determine if it is safe.
You can alsocheck the certificate of the EXE file . An authentic file will have a security certificate issued by Microsoft. If you see anything else, it is likely to be malicious.
The final thing to do is scan suspect files with an up-to-date antivirus scanner. Quarantine and remove any files that are flagged as infected. Fortunately, modern versions of Windows come with Microsoft Defender built-in, so learnhow to scan a single file or folder with Microsoft Defender to check any suspicious files you find.
The Windows Processes That Might Be Hiding a Virus
Part of keeping your Windows PC safe from malware and viruses is knowing where they hide. Sometimes a malicious file will behave oddly, using too much CPU and memory. But not always. So spotting a suspicious file in other ways is a useful skill.
Also read:
- [Updated] 2024 Approved Beginner's Handbook for PC Users - Initiating a TikTok Broadcast
- 10 Proven Strategies to Solve Windows Update Woes
- 2024 Approved How to Shoot a Green Screen Video
- 5 Secure Windows Strategies When Bitlocker Fails
- Addressing “Lunar Client Startup Failures” On Windows Systems
- Advanced SFX Strategies for Windows 11 Users
- ASUS Zenbook 14 OLED (UX3405) Review: Is This the MacBook of Windows?
- Best Google Pattern Lock Removal Tools Remove Android Pattern Lock Without Losing Data
- BitLock Cracked: Staying Secure Yet Unmoved
- Google Play Services Wont Update? 12 Fixes are Here on Xiaomi Redmi Note 13 Pro 5G | Dr.fone
- In 2024, How to Turn Off Find My Apple iPhone 13 Pro Max when Phone is Broken? | Dr.fone
- In 2024, Mastering Zoom Meetings on Chromebooks
- Navigating TikTok Media on Chrome Devices Effortlessly for 2024
- Overcome Windows Obstacles: Expert Advice Awaits
- The 10 Best Tools to Bypass iCloud Activation Lock On Apple iPhone XS Max You Should Try Out
- Top Sites for Streaming Lower-Resolution Anime Content (144P, 240P, 360P, and More)
- Title: Seven Crucial Windows Functions to Monitor Vigilantly
- Author: Richard
- Created at : 2024-11-16 17:29:01
- Updated at : 2024-11-17 17:26:24
- Link: https://win11-tips.techidaily.com/seven-crucial-windows-functions-to-monitor-vigilantly/
- License: This work is licensed under CC BY-NC-SA 4.0.