
Unveiling Alternatives to Traditional UAC Practices on Windows

Unveiling Alternatives to Traditional UAC Practices on Windows
If you’ve ever tried running a program on Windows as an administrator, you’ve probably come across a prompt asking you to either give or deny it permission to make high-level changes. That’s User Access Control (UAC) in action, and it adds an extra layer of security when a program or task is seeking elevated privileges. This gives you the chance to stop unwanted or malicious software from making changes on your PC.
As an administrator, you can change how UAC behaves. In this guide, we’re going to show you how to do that using the Local Group Policy Editor and Registry Editor.
Disclaimer: This post includes affiliate links
If you click on a link and make a purchase, I may receive a commission at no extra cost to you.
What Behaviors Does UAC Have for Administrators?
Before you go about changing the way UAC acts for administrators, it helps to know what behaviors you can choose and what they mean. We’re going to list them below, along with the definitions that are listed on Microsoft Learn .
Here’s what you can choose:
- Elevate without prompting: Assumes that the administrator will permit an operation that requires elevation, and more consent or credentials aren’t required. This minimizes the protection that is provided by UAC.
- Prompt for credentials on the secure desktop: When an operation requires elevation of privilege, the user is prompted on the secure desktop to enter a privileged username and password. If the user enters valid credentials, the operation continues with the user’s highest available privilege.
- Prompt for consent on the secure desktop: When an operation requires elevation of privilege, the user is prompted on the secure desktop to select Permit or Deny. If the user selects Permit, the operation continues with the user’s highest available privilege.
- Prompt for credentials: An operation that requires elevation of privilege prompts the administrator to type the username and password. If the administrator enters valid credentials, the operation continues with the applicable privilege.
- Prompt for consent: An operation that requires elevation of privilege prompts the administrator to select Permit or Deny. If the administrator selects Permit, the operation continues with the administrator’s highest available privilege.
- Prompt for consent for non-Windows binaries: This prompt for consent is the default. When an operation for a non-Microsoft application requires elevation of privilege, the user is prompted on the secure desktop to select Permit or Deny. If the user selects Permit, the operation continues with the user’s highest available privilege.
Now that you’re familiar with the UAC behaviors for administrators, let’s see how to change them.
Changing UAC Behavior for Administrators in the Local Group Policy Editor
To change the UAC behavior for admins using the Local Group Policy Editor (LGPE), start by pressing Win + R, typing gpedit.msc in Windows Run, and hitting the Enter key to open the LGPE on Windows .
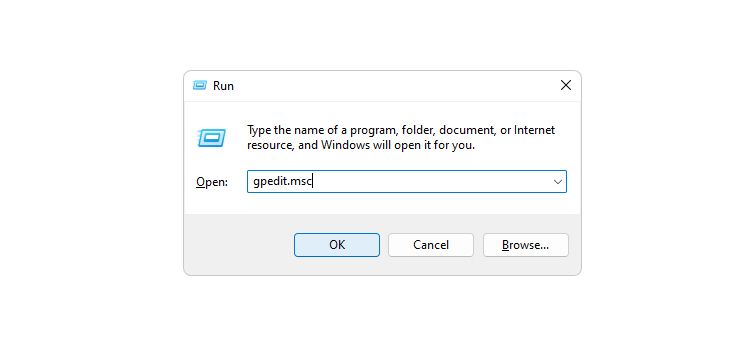
In the left panel, navigate to Configuration > Windows Settings > Security Settings > Local Policies > Security Options. In the right panel, double-click the User Account Control: Behavior of the elevation prompt for administrators in Admin Approval Mode policy to access its Properties window.
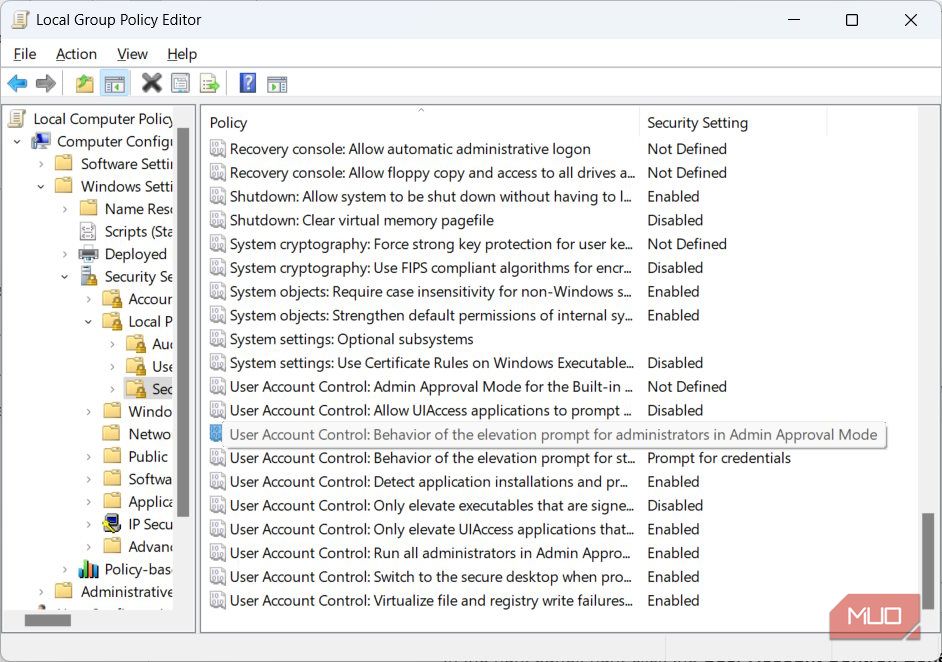
Click on the dropdown and select the UAC behavior you want.
To apply and save the changes, click on OK.
Changing UAC Behavior for Administrators in the Registry Editor
To change the UAC behavior for administrators using the Registry Editor, start by pressing Win + R, typing regedit in Windows Run, and hitting the Enter key.
In the UAC prompt, click Yes to open the Registry Editor on Windows .
Changing settings in the Registry Editor can impact the performance of your computer negatively if you make a mistake. To make sure you always have a way to revert the changes, we recommend learning how to back up and restore the Windows Registry .
In the navigation panel on the left, head to HKEY_LOCAL_MACHINE > SOFTWARE > Microsoft > Windows > CurrentVersion > Policies > System. In the right panel, double-click the ConsentPromptBehaviorAdmin value to modify it.
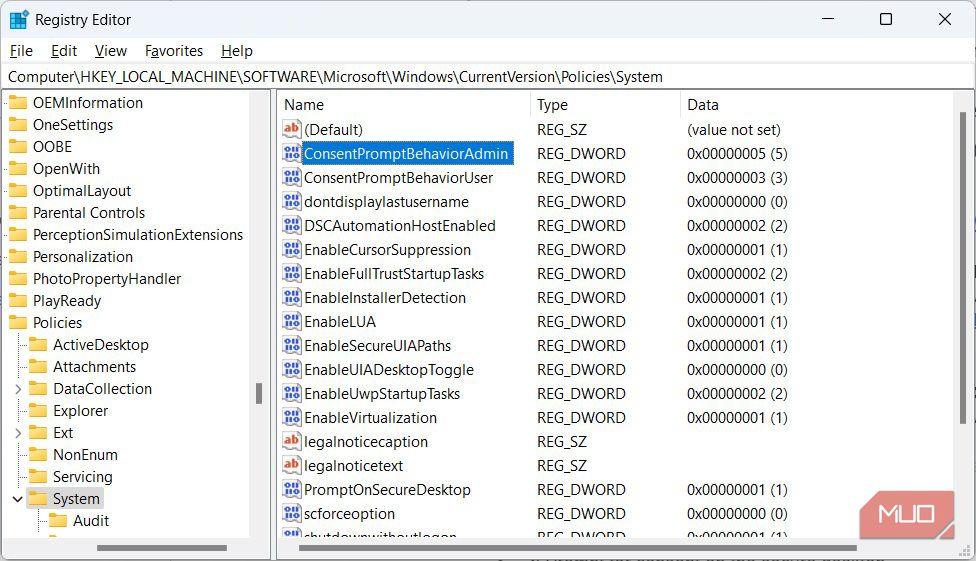
Enter one of the following variables in the text box for Value date:
| Variable | UAC Behavior |
|---|---|
| 0 | Elevate without prompting |
| 1 | Prompt for credentials on the secure desktop |
| 2 | Prompt for consent on the secure desktop |
| 3 | Prompt for credentials |
| 4 | Prompt for consent |
| 5 | Prompt for consent for non-Windows binaries |
So, if you were to, for example, change it to Prompt for credentials, you’d enter 3 in the Value data text box.
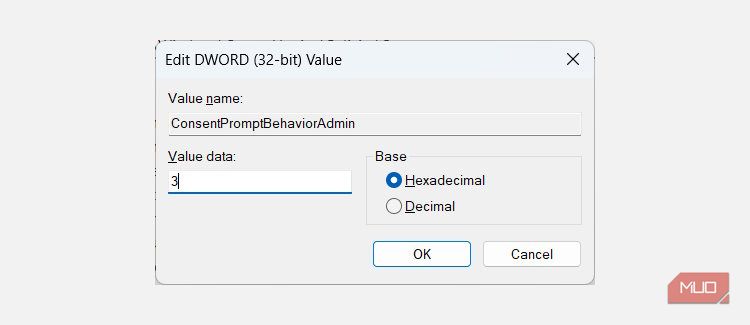
Then, click OK to apply and save the changes.
Control the UAC’s Behavior as an Administrator
Now you can change the behavior of UAC for admins as you please, depending on your situation. Just be careful not to make your computer more vulnerable in the process, which can happen if you choose Elevate without prompting. Microsoft recommends using that option only when you’re in a highly secure environment where the administrator accounts are tightly controlled.
In that case, you can even disable the UAC altogether if you’d like since you know there are other measures in place to protect your computer from unwanted or malicious programs.
As an administrator, you can change how UAC behaves. In this guide, we’re going to show you how to do that using the Local Group Policy Editor and Registry Editor.
Also read:
- [New] Pixel Pizzazz Top 10 Screenshot Sticker Enhancers for iPhones/Androids
- [Updated] Transformative Ways to Document FaceTime Interactions
- 10 Free Location Spoofers to Fake GPS Location on your Nokia 105 Classic | Dr.fone
- HP Sound System Issues Corrected for Windows 11/8/7 Users – Easy Solutions Inside!
- Immediate Fixes for Hitching Windows Tasks
- In 2024, Pinnacle of Plot Construction – The World's Best 8 Academies
- Mastering Permanent Erase: Configuring a Trash Bin for Irreversible Deletion in Windows PCs (11)
- Mastering Virtual Memory Settings to Power Windows 11 Systems
- Mistral AI's Le Chat Vs. ChatGPT: Our Comprehensive Comparison
- Orchestrating a Journey Through Hidden YouTube Archives
- Steam UI DLL Failure: Fixing the 'Failed to Load steamui.dll' Critical Steam Issue
- The Art of Theme Creation in Windows Terminal
- The Ultimate Walkthrough for Implementing Hyper-V Technology in Windows 10
- Unlock Windows Boots with 5 Key Fixes to Security Errors
- Win Over a Shaky Desktop Pointer with These Steps
- Title: Unveiling Alternatives to Traditional UAC Practices on Windows
- Author: Richard
- Created at : 2024-11-16 17:59:51
- Updated at : 2024-11-17 20:29:44
- Link: https://win11-tips.techidaily.com/unveiling-alternatives-to-traditional-uac-practices-on-windows/
- License: This work is licensed under CC BY-NC-SA 4.0.